Cyberrisk is not only headline news, but also a priority for senior executives. Risk managers in various industries now consider cyberrisk to be the biggest threat to their business, ahead of compliance issues and financial risk.
Business continuity and crisis management are crucial aspects of cybersecurity, irrespective of the industry you are in. The threat is growing.
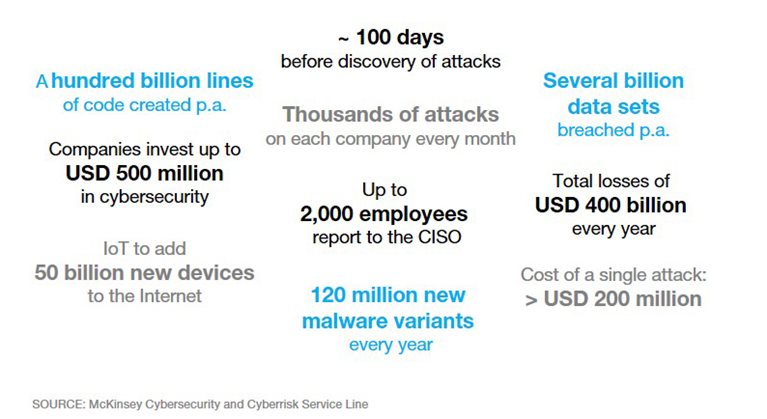
While hackers are honing their skills, refining their techniques, and industrializing their craft, a number of business trends – although inherently unrelated to cybersecurity – make companies more vulnerable to cyberattacks.
- The digitization of the entire value chain means that various assets – ranging from the design of new products and services to distribution networks and customer data – are now at risk.
- At the same time, the complexity of corporate digital value chains is growing. Typically, these value chains span thousands of people, countless applications, and a myriad of servers, workstations, and other devices.
- Thanks to outsourcing and offshoring, the weakest link of a company’s value chain may well be a supplier or other third party.
The good news is that awareness of the magnitude of the threat is growing. According to a recent McKinsey survey, 75 percent of experts consider cybersecurity to be a top priority for their businesses. The bad news is that executives are overwhelmed by the challenge. Only 16 percent say their companies are well prepared to deal with cyberrisk. Common pitfalls are:
- Delegating the problem to IT
- Throwing resources at the problem
- Treating the problem as a compliance issue.
An adaptive, more comprehensive, and more collaborative approach to cyberrisk is needed. Comprehensive cyberrisk management comprises multiple approach.
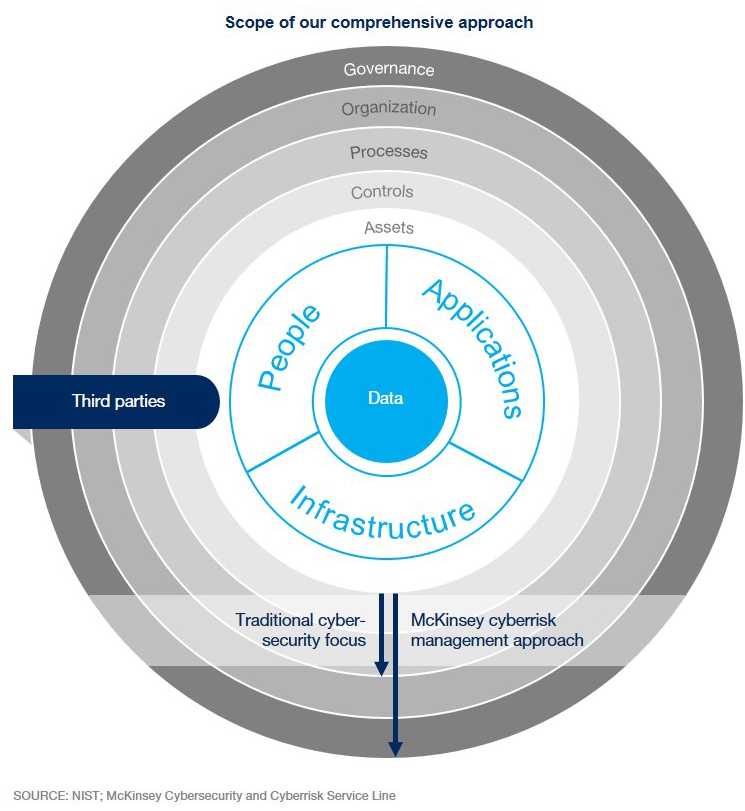
Eight key recommendations
- Treat cyberrisk as a strategic risk, rather than a technical issue.
- Make business leaders accountable for their areas of cybersecurity.
- Create transparency on relevant threats, critical assets, and effective controls to focus your investments.
- Ramp up the skills of your cyberrisk teams and the seniority of your cyberrisk leaders.
- Get ready for the Internet of Things and Industry 4.0 by extending your cyberrisk efforts beyond IT applications and infrastructure.
- Make it easy for employees to do the right thing by providing efficient cybersecurity solutions that don’t restrict agility and innovation.
- Invest in response and recovery as much as you invest in resilience.
- Pay special attention to subsidiaries, contractors, and service providers. Third parties are typically one of the most vulnerable parts of your value chain.